11 sett 2017 anni - FireEye removed an Equifax case study
Descrizione:
https://www.theregister.co.uk/2017/09/11/equifax_incident_response_omnishambles/https://krebsonsecurity.com/2017/09/equifax-breach-response-turns-dumpster-fire/
https://medium.com/contratastic/a-series-of-unfortunate-events-or-how-equifax-fire-eye-threw-oil-on-the-fire-c19285f866ed
FireEye removed an Equifax case study* from its website in response to a recently disclosed mega-breach at the credit reference agency.
Equifax’s endorsement that FireEye’s tech protected it against zero-day and targeted attacks had more than the whiff of hubris about it once it emerged hackers had successfully pwned the credit reference agency’s systems and accessed all manner of sensitive information.
Equifax back FireEye for hacker defence
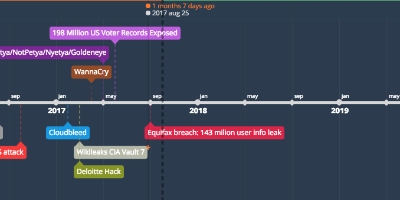
The breach, discovered in late July but disclosed only last Thursday, affected 143 million US consumers and an as-yet undisclosed number of Brits and Canadians.
The intrusion began in mid-May and went undetected for two months until 29 July. Criminals had access to names, social security numbers, birth dates, addresses and, in some instances, driver’s license numbers of millions of Americans as well as the credit card numbers of 209,000 US consumers.
Early indications are that hackers failed to go even deeper and access Equifax’s core consumer or commercial credit reporting databases. Equifax said that hackers exploited an unspecified web application vulnerability to hack into its systems.
Equifax has reportedly hired incident response experts at FireEye Mandiant to investigate the breach. These experts have also been helping with PR aspects of damage limitation, it seems. Brandan Schondorfer of Mandiant registered the domain Equihax.com on Tuesday (5 September), two days before the breach was publicly disclosed, thereby preventing anyone else intent on poking fun at Equifax – or perhaps worse, run phishing attacks – from getting their hands on the domain.
Other aspects of Equifax’s overall incident response (analysed in depth in a post by security blogger Guise Bule here) have been less assured. For example, security experts at Sophos have criticised Equifax’s use of PINs – based on the date and time of when a request was made – to freeze consumer credit files. Crooks have a far better chance of determining these PINs and unfreezing credit files than if they were randomly generated. Worse yet, compromised server logs might be used to determine PINs. ®
Aggiunto al nastro di tempo:
Data:
11 sett 2017 anni
Adesso
~ 8 years ago